Network segregation is a popular security measure that keeps your business's sensitive data and systems safe from malicious cyberattacks. To put it simply, network segmentation divides your organization's computer infrastructure into separate networks to create an effective defence against hackers. This practice allows businesses to limit access to specific areas of their network, ensuring only authorized personnel can access the sensitive information stored within. With the right network segmentation strategy in place, businesses can enjoy maximum protection from cybercrime without sacrificing efficiency or speed.
In the following sections, we'll look at the benefits of using network segmentation for business, analyze different types of strategies used to maximize security and efficiency, discuss how to implement a robust network segmentation strategy in your business environment, explore cybersecurity considerations when using network segmentation, and list best practices for maintaining secure networks with effective segmentation strategies. Plus, we'll look at case studies on successful implementations of network segmentation in businesses to help you gain valuable insights from real-world examples. So let's get started!
What is Network Segregation?
Network segregation is an important cybersecurity strategy for businesses of all sizes. It involves logically or physically separating a larger computer network into smaller segments that are easier to manage and secure from cyber-attacks. Each segment can contain different types of network components, users, applications, and resources. This way, if one segment of the network is compromised, it won’t spread to other areas in the same way as it would if they were all connected in one large system.

Benefits of Network Segregation for Businesses
• Increased security: By isolating different parts of the network, businesses can reduce their vulnerability to a wide spectrum of cyber threats. It’s an excellent way to ensure unauthorized personnel don’t gain access to sensitive information or critical systems.
• Improved scalability and flexibility: Network segregation makes it easier for organizations to scale their IT infrastructure as needed without compromising performance or reducing security. This enables businesses to quickly adjust and adapt their networks for maximum efficiency and productivity.
• Simplified management: Splitting up networks into multiple smaller segments makes them much easier to manage in terms of installation, configuration, monitoring, and maintenance tasks. With segmentation, there’s less risk of experiencing outages due to improper maintenance.
• Reduced overhead costs: Implementing network segmentation can help businesses save time and money in the long run since it eliminates unnecessary expenses associated with unauthorized access or malicious attacks.
Types of Network Segregation Strategies for Maximum Security and Efficiency
There are several types of network segregation strategies that businesses can implement for maximum security and efficiency:
• Physical separation: This strategy involves physically separating network components, such as servers and routers, into different physical locations. It’s often used by enterprises that need to maintain high levels of privacy and security.
• Virtual LAN (VLAN): A VLAN is a virtual network that can be separated from other networks on the same physical segment. It offers additional control over broadcast traffic, allowing businesses to easily segment their networks while boosting performance and scalability.
• Subnets: Subnetting is a method used to divide an IP address space into multiple subnets in order to create smaller logical segments within the same physical network. It’s commonly used by larger organizations with complex IT infrastructures.
• Firewalls: Firewalls are used to create a barrier between the internal network and potential external threats. They can be configured with rules to limit access from certain IP addresses or regions, making it easier for businesses to control who has access to their systems.
How to Implement a Robust Network Segmentation Strategy in Your Business
Implementing a robust network segmentation strategy requires careful planning and consideration of security objectives. Here are some steps you should take when creating your own strategy:
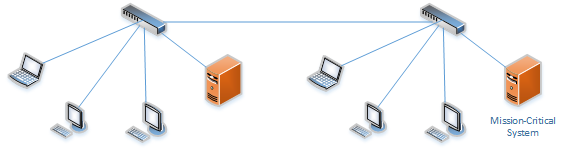
• Identify the different types of assets you need to protect: These could include important data, applications, users, or other assets that are integral to the functioning of your business. Make sure these assets are separated into distinct segments to ensure maximum security.
• Assign the right access privileges: Ensure that different users have appropriate levels of access to the network, depending on their roles and responsibilities. This will help you reduce the risk of unauthorized personnel accessing critical systems or information.
• Monitor traffic patterns: Regularly monitor your networks for any suspicious traffic patterns or anomalies that could indicate malicious activity. This includes monitoring user activities such as logins, file transfers, and data usage.
• Automate processes where possible: Automating certain processes within the network can make it easier to manage and maintain segmentation policies over time. Examples include implementing automated firewalls and intrusion detection systems (IDS).
Cybersecurity Considerations When Using Network Segmentation
• Make sure users follow the correct procedures: It’s important that all users are aware of and comply with the necessary security protocols when accessing the network. This includes using strong passwords, avoiding suspicious links, and not sharing confidential information.
• Regularly update software and systems: Outdated software or hardware can create vulnerabilities which can be exploited by malicious actors. Therefore, make sure all systems are regularly updated with the latest patches to ensure maximum security.
• Monitor for potential intrusions: Monitor your networks for any unauthorized access or attempts at exploiting vulnerabilities in your system. Also, consider investing in intrusion detection systems (IDS) to detect suspicious activity on your networks in real-time.
• Encrypt sensitive data: Data encryption is an effective way to protect confidential information from third-party access. Consider encrypting all sensitive data both in transit and at rest, as well as using multi-factor authentication (MFA) for added security.
• Implement a backup plan: Make sure you have a backup and disaster recovery plan in place. This ensures that your business can quickly recover from any malicious activity or disasters that may occur.
Best Practices for Maintaining Secure Networks with Effective Segmentation Strategies
• Conduct regular network audits: Regularly audit your networks to ensure they are properly configured and operating securely according to the latest industry standards. This includes testing for potential security flaws and vulnerabilities, as well as ensuring all segmentation rules are up to date.
• Educate employees: Make sure all members of staff are aware of your network policies and the importance of following them correctly. Regularly educate employees on cyber threats and best practices to help reduce the risk of malicious activity or data breaches.
• Leverage tools and technologies: Utilize a combination of tools and technologies to manage your network segmentation strategy more effectively. Examples include automated firewalls, intrusion detection systems (IDS), VPNs, and access control systems (ACS).
• Implement enterprise-wide policies: Establish a comprehensive set of policies that govern how users access networks and systems, as well as what data should be accessible. Make sure these policies are communicated to all members of staff to ensure they understand the importance of following them correctly.
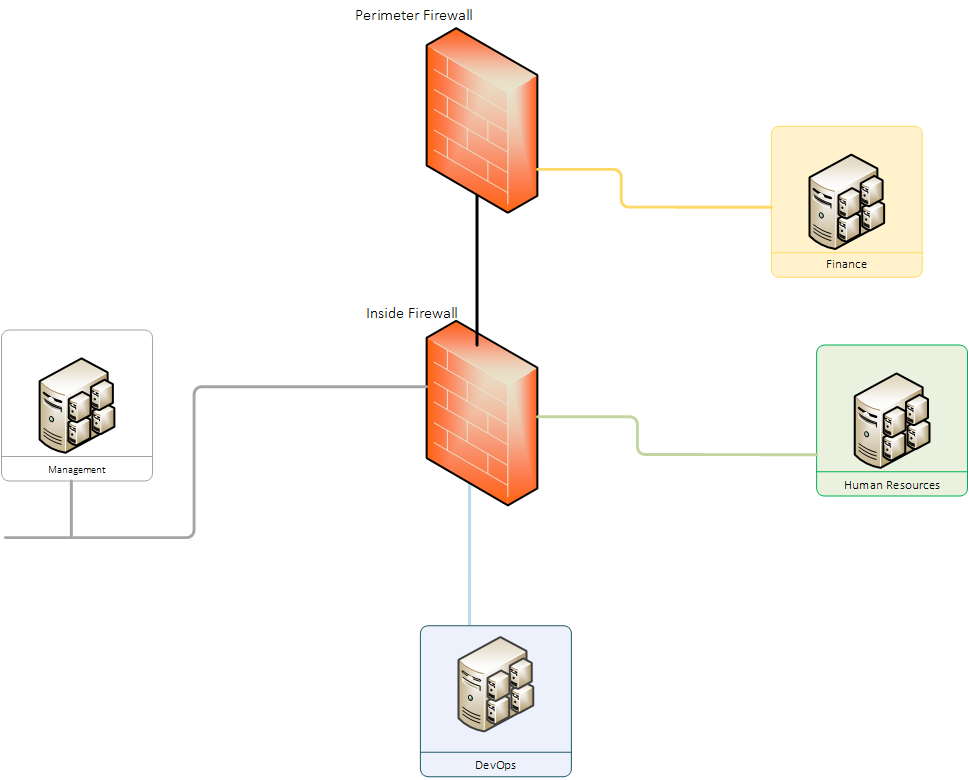
Troubleshooting Common Issues with Network Segmentation
• Misconfigured segmentation rules: Misconfigured segmentation rules can lead to unauthorized access or data breaches. To prevent this, regularly review your policies and make sure any changes are properly documented and tested before implementation.
• Lack of visibility over user activities: Without proper monitoring tools in place, it’s difficult to have full visibility over user activities within the network. Consider investing in a network monitoring tool to provide real-time visibility over user activities and detect any suspicious behaviour.
• Slowdowns in performance: If the network becomes overloaded, it can cause slowdowns in performance. To prevent this, make sure your segmentation policies are optimized for maximum efficiency and that resources are allocated appropriately.
• Unauthorized access: A lack of proper security controls can lead to unauthorized access or data breaches. To protect against this, make sure you have robust authentication processes in place as well as an up-to-date firewall configured correctly.
Case Studies on Successful Implementation of Network Segmentation in Businesses: Lessons Learned from Real-World Examples
One successful example of network segmentation can be found at a large e-commerce company. This company successfully implemented segmentation rules to separate its customer-facing web applications from its internal networks and databases. In addition, they set up automated firewalls to monitor traffic flows and detect any malicious activity in real-time. As a result, they were able to reduce the risk of data breaches and enhance the overall security of their network infrastructure.
Another case study involves an international enterprise that implemented segmentation rules to ensure compliance with industry regulations. By segregating its sensitive customer data from publicly accessible systems, the company was able to meet all regulatory requirements while also enhancing its overall security posture.
These case studies show that network segmentation can be a powerful tool for businesses of all sizes. By following the best practices outlined in this article, you too can improve your security posture and reduce the risk of data breaches.
